SRM was another 50 point reverse engineering challenge at SharifCTF 2016. A binary was provided with the following description:
The flag is : The valid serial number.
file reported that the binary was a PE32 for Windows. So I fired up a Win7 VM and pulled up the disassembly in IDA.
Running the binary resulted in a dialog asking for an email address and a serial number.
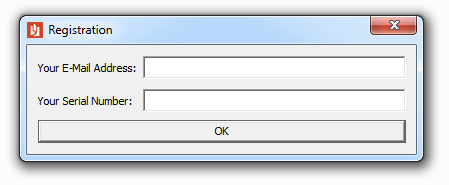
A few quick test inputs showed that there was some validation of email address field and guesses at the serial resulted in ‘Registration Failure’ responses.
Looking at the file in IDA, DialogProc seems to handle all the logic. The HexRays decompiler failed to recognise the static array that is populated by the user’s input from the textBox.
After fixing the datatype definition to CHAR[16] (Set IVAR Type from the context menu or ‘Y’ hotkey) the checks made later in the code become clear:
if ( strlen(KeyString?) != 0x10
|| KeyString?[0] != 'C'
|| KeyString?[15] != 'X'
|| KeyString?[1] != 'Z'
|| KeyString?[1] + KeyString?[14] != 0x9B
|| KeyString?[2] != '9'
|| KeyString?[2] + KeyString?[13] != 0x9B
|| KeyString?[3] != 'd'
|| KeyString?[12] != '7'
|| KeyString?[4] != 'm'
|| KeyString?[11] != 'G'
|| KeyString?[5] != 'q'
|| KeyString?[5] + KeyString?[10] != 0xAA
|| KeyString?[6] != '4'
|| KeyString?[9] != 'g'
|| KeyString?[7] != 'c'
|| KeyString?[8] != '8' )
We can see that much of the desired input is hardcoded. The remaining three items can be derived from the existing data:
KeyString[14] is 0x9b - Keystring[1] (‘Z’ or 0x7a)
Result: 0x41 (‘A’)
Calculating the rest of the derived characters results in the string:
CZ9dmq4c8g9G7bAX
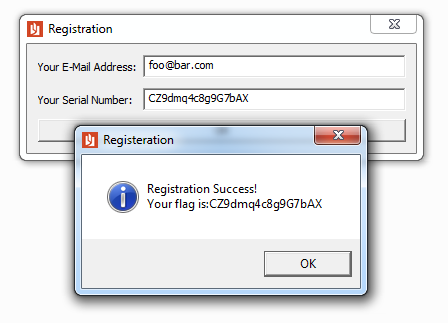
Entering this key with a valid email address results in a ‘Registration Successful’ message and gives the flag for the challenge.