The lowest scoring challenge at Kaspersky’s 2017 CTF turned out to be a pretty tricky. Mainly due to weird flag formatting, but also because I am stupid and couldn’t see a blatant clue staring me in the face.
Challenge
Hey! Do you like playing? Are you old school?
Have fun!
Concat answer to KLCTF prefix
Solution
A .bin file could be just about anything, so I ran strings, binwalk and the usual suspects against it in the hope of an easy flag, but didn’t find anything. So the next step was to fire up a hex editor to see if there were any clues in the file content.
The NES string in the header suggests a Nintendo Entertainment System ROM.
4E 45 53 1A 02 01 01 00 NES.....
00 00 00 00 00 00 00 00 ........
The file command managed to identify the file and confirm this. I have been favouring binwalk for a while, but this shows that you shouldn’t rule anything out.
I had the rather excellent FCEUX NES emulator installed already, so I threw the file in there and fired it up.
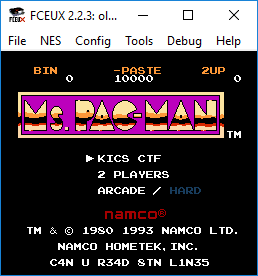
We seem to have a Ms PacMan game.
Some of the text seems to have been tampered with, but nothing leapt out, so I started to play the game.
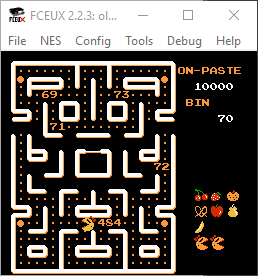
Level one looked normal, but level two had some odd numbers scattered around the maze.
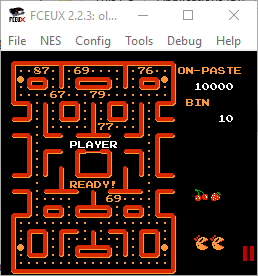
Playing on, I managed to get to level 3 before running out of lives. This level also had some extra content.
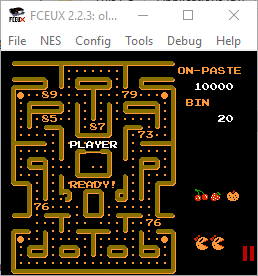
Taking the mystery values and converting to ASCII showed that I was on the right track:
87 69 76 67 79 77 69
W E L C O M E
89 79 85 87 73 76 76
Y O U W I L L
However, I needed to see more levels to get the rest of the info and I’m not that great at Ms Pacman, especially as the controls seemed a bit fiddly when trying to hit the turns.
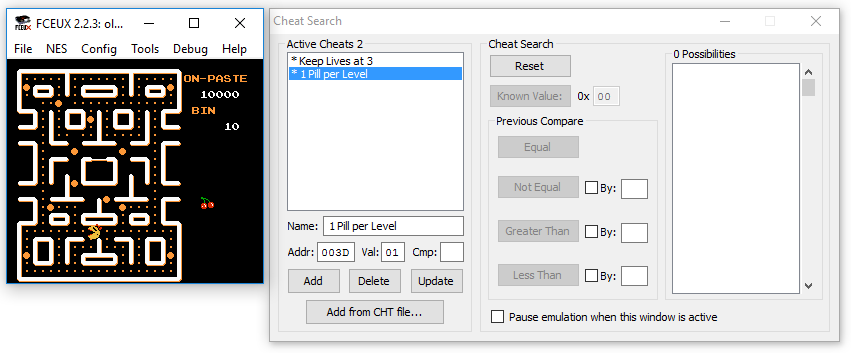
FCEUX has a great disassembler and debugger to help out here. My 6502 assembler isn’t that great, but code is code and there must be a variable that keeps a count of lives somewhere.
It turns out that NES game developers liked to use the first page of RAM on the system for variables because the addresses could be referenced in one byte, keeping the code tidy and compact. This means we have a nice small area to hunt for interesting data in. FCEUX has a great memory watcher that allows us to track the values in RAM with useful info like previous values and change counts. This made it simple to find that the life counter value was stored at 0x3F.
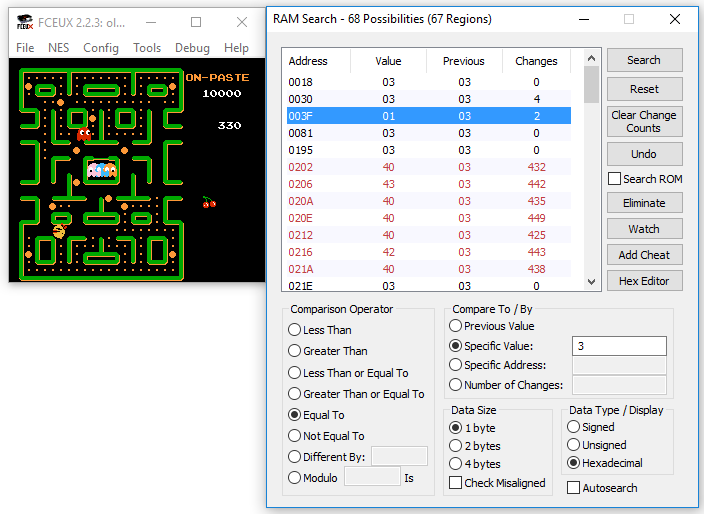
Using the cheat editor, I was able to pin 0x3F at 3, giving me infinite lives. This removed the block on getting to the later levels but I still had to do the time consuming work of steering Ms Pacman around the maze to finish each level.
Because I am lazy (and bad at Ms Pacman), I used the memory tracker to work out that 0x3D was a counter that was decremented every time a ‘pill’ was eaten on the screen. When the counter hits zero, the level completion routine fires. Another quick cheat was created to set 0x3D to 1. This has the effect that the level is completed as soon as a single pill is eaten.
Now I was able to spin through the levels in no time.
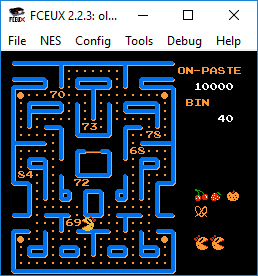
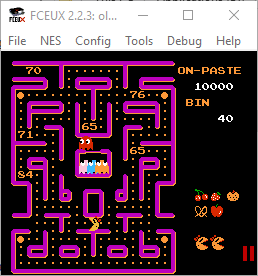
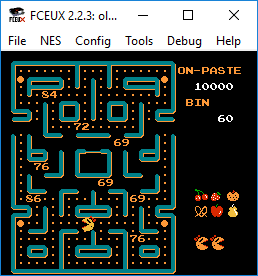
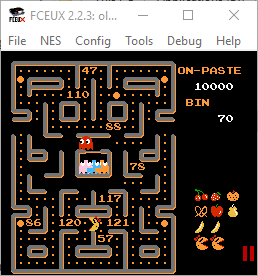
After level 8 the numbers stopped appearing. I did sit through a bunch of extra levels and the god awful ‘cutscenes’ just to make sure.
Time to decode the numbers:
Level 2
87 69 76 67 79 77 69
W E L C O M E
Level 3
89 79 85 87 73 76 76
Y O U W I L L
Level 4
70 73 78 68 84 72 69
F I N D T H E
Level 5
70 76 65 71 65 84
F L A G A T
Level 6
84 72 69 76 69 86 69 76
T H E L E V E L
Level 7
69 73 71 72 484
E I G H T
Level 8
47 110 88 78 117 86 120 121 57
/ n X N u V x y 9
Simple right? No, this is where the real fun began.
I assumed the ‘/n’ was a newline and tried to submit the flag as KLCTF{XNuVxy9}. Nope. After trying loads of variations and getting pretty fed up it was pointed out to me that the modified text saying ON-PASTE and BIN in the game was a clue.

Sure enough, at Pastebin.com/nXNuVxy9 I discovered the some info:
G00dJ0b
S0xGQ1RGe1czXzRMTF9MMFYzX1IzVFIwfQ==
This is pretty obviously Base64 encoded to prevent Google giving the game away. The resulting text is:
KLFCTF{W3_4LL_L0V3_R3TR0}
Yay!

This flag was still rejected by the scoreboard. The extra ‘F’ in the prefix was a nice nod to 90s British Electronica but wasn’t helpful. After another session of trying different many variations, I went off to bed in a sulk.
It was only when a suggestion of removing the braces (and the extra ‘F’) from the flag worked that I was able to find peace.
KLCTFW3_4LL_L0V3_R3TR0

Kaspersky’s CTF had some nice ideas for unusual challenges, but it seems that a few challenges were made unreasonably difficult by inconsistent flag formats.
Thanks to @jimhalfpenny and @MattWhatkins for keeping me sane.